Every webmail service out there, be it Gmail, Yahoo, Hotmail, or other, encourages you to upload or merge your contacts with their system. And most Mac and PC email programs automatically cross-reference an incoming email sender with their entry in your contacts. The result is often that their contact profile picture, and ‘friendly’ name, is displayed as the sender of that email in your inbox.
This is a very serious issue to which nearly every email program is vulnerable. Please share this information not only with your friends and loved ones, but also your workplace and colleagues. You can also email it, print it, or save it to Evernote using the buttons at the top, bottom, and left-hand side of this article.
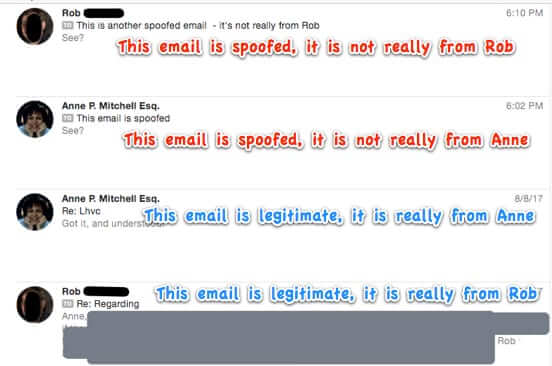
Typical View of Email Inbox
The above is a fairly typical view from an email inbox. Pictured are two legitimate emails, displaying the contact image and name of each email sender. Now, look at this screen capture of the same email inbox:
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.
Most people will look at those emails and never in a million years imagine that two of them are fake, and not from the person that their system is telling them that it’s from.
Spoofing Email: The act of sending an email that appears to be from someone else.
So, how easy is it to spoof email? The real-life example above took the spoofing sender (someone on our staff) less than five minutes, from start to finish – including the time that it took to search for and find an email spoofing service.
The combination of these familiar images demonstrating who the email is supposedly from, combined with the ease of spoofing, makes it very easy for a scammer to use social engineering to have the recipient take some action at the request of the scammer, as the recipient automatically believes it’s the person represented in the image and name.
This is exactly what happened to a company called Medidata, leading to them send over $4,000,000 to a scammer who was posing as the president of the company by simply spoofing the president’s email address. Just like our example above.
Medidata happens to use Google apps to process their mail, but this could have happened regardless of what system they used.
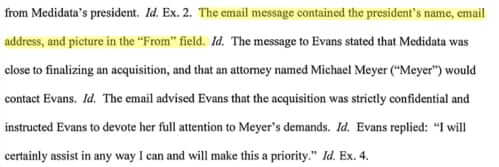
A scammer spoofing Medidata’s president’s email address sent an email to a clerk in Medidata’s accounts payable department. The email contained the president’s name, his email address, and picture in the “From” field.
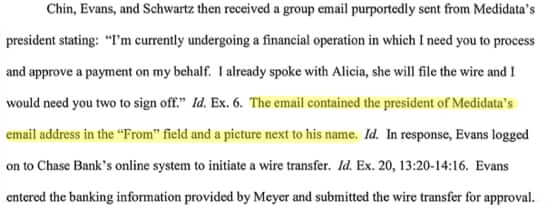
Next several executive officers of Medidata received a group email “from” Medidata’s president. This email also contained the president’s name, email address, and picture next to his name in the “From” field.
This fairly simple scam led to Medidata wire transferring $4,770,226.00 to the scammers. That’s four million, seven hundred seventy thousand, two hundred twenty six dollars.
There is no doubt at all that the fact that the emails carried that reassuring image of the president’s face, along with his name and email address, in the “From” field, lulled the accounts payable clerk, and the company officers, to never even imagine for a moment that the email did not originate from the president.
It never crossed their mind.
Why would it?
It was only because one of them thought that there was something fishy about the reply-to address of a subsequent email that they didn’t send a second wire transfer!
So, how did those scammers manage to insert Medidata’s president’s image in their spoofed email – let alone the correct image?
That’s exactly the point of this article. They didn’t!
They relied on the fact that so many email systems now display the contact’s avatar or icon in the email, based on the sending email address alone, which is in the recipient’s contact program or list of contacts – and, which can be very easily spoofed, tricking the programs.
Let us repeat that, because it’s extremely important:
Your email program will display the “sender’s” image and name to you – soft-verifying who it is from (even if it isn’t) – based only on the email address that it finds in the “From” field.
So if you believe in the authenticity, veracity, and security of your email based on seeing your friend’s or colleague’s smiling face attached to that email, you are ripe for being scammed this way.
Look at this picture again:
The spoofed emails are indistinguishable from the real ones. All the sender had to do was to go to a site that allows you to send spoofed email, and spoof the “From” address of a sender in my contacts. My own email program did the rest.
And so will yours.
And so will your company’s. And your company’s employees’ programs.
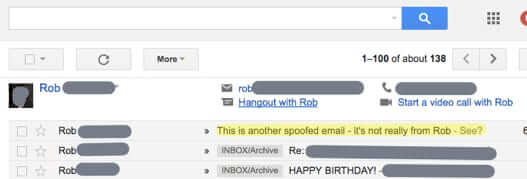
Here is an example of that same spoofed email as it hits Gmail:
Note that Gmail, even with its aggressive spam filtering, did not put this spoofed message in the spam folder, even though the spoofed address was a Gmail address, and this spoofed email did not actually originate from Gmail.
Google did put the little red unlocked padlock in the message, and a warning that it may not really be from Rob, but you’d have to open the message to see that. And as we, like Medidata, and so many others, only use Google to pass email on to our own machines, we’d ordinarily never see that.
So, what is to be done about this ubiquitous social vulnerability?
Well, of course, forewarned is forearmed, so please share this information with your friends and colleagues.
In fact forward it to them, and to your IT department, sysadmins, security officers, etc..
But that’s hardly enough.
There are products and services out there, such as Barracuda’s email security gateway, that check for spoofing and look for proper domain authentication (i.e. check that the domain that the email says that it is from is the domain that really sent it, unlike the spoofed Gmail address in our example).
The problem with solutions like Barracuda’s is that lots of legitimate senders still do not have their email sending authentication (such as DMARC, DKIM and SPF) set up correctly, so that if you reject any email which isn’t properly authenticated, you are likely to reject a lot of email that you actually want to receive.
Regardless of what else you do, we advise email receivers – and particularly businesses – to turn off contact images being displayed in email, and even turn off the so-called “friendly names”, so that what is displayed is the email address. At very least, your employees won’t be given that false sense of security and recognition by seeing the image of the contact displayed, and may even catch something ‘not quite right’ (such as the Medidata person did with the “Reply-to” address).
Speaking of Medidata, this was actually the subject of a very recent lawsuit (decided on July 21, 2017) in New York based on Medidata’s insurance company, Federal Insurance, refusing Medidata’s insurance claim for the $4,770,226.00, under the Computer Fraud part of their insurance policy (Medidata won – you can read the full court decision here).
If you have any other ideas for how to deal with the issue of (spoofed) email addresses pulling in contact images and names, making the fake email seem more believable, we’d love to hear them!
[Note: This is a very serious issue to which nearly every email program is vulnerable. Please share this information not only with your friends and loved ones, but also your workplace and colleagues. You can also email it, print it, or save it to Evernote using the buttons at the top, bottom, and left-hand side of this article.]
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.










My work platform and my personal platform for email are both Google. I cannot find a way to turn off “sender images” or “friendly email” – do you have a how-to for readers?
Hi Jackie – unfortunately at this time we are unaware of any way to do this in Gmail. Gmail is great for using as a spam filter, but not great as an actual email client (at least in our opinion). Here at TIP, we run our email through Gmail, but then download it into our computer’s email program (in our case Mac mail).
The solution(ish) for this is strong per-user cryptographic signatures on essentially all personal email, both business and non-business. There are 2 mature open standards for this, each of which has multiple inter-operative implementations: S/MIME and OpenPGP. Without a valid signature of a trusted sender, a message should not be “prettified” in any way. Rather it can be “uglified” in various ways depending on the particular failings: signature existence, signature validity, or trust. There are MUAs (e.g. MailMate on MacOS, TBird with the right assembly of extensions…) which do this to some degree. Webmail providers could in theory do it quite robustly. But they don’t.
That’s a symptom of why pervasive strong signatures on email is only “solution-ish.” The root cause is that users (and by extensions companies who outsource email to providers like Google and MS who got their start in email by providing services so shoddy they were free.) do not want email to be nuanced, ugly, or expensive. Making everyone use crypto means someone needs to do tech support for whatever crypto tools are used. That’s a cost. Adding obtrusive security warnings and disabling HTML rendering and/or header or inline graphics display is ugly. A message can be distrusted in about half a dozen different ways, some of which are less serious than others and some of which the recipient can “fix” either wisely or foolishly. So users need training they do not want to need to understand details they’d rather not know. Nuance AND cost.
People use this solution every day in fully-functional organizations. Those organizations spend more on tech support and user training. They demand more skills and mindfulness from their users. They are rare because no one has made the case well to most businesses for why the added cost and effort is worthwhile.
I think the moral of the story, is that before before transferring large sums of money, always get voice confirmation. Do not rely merely on emails. And always have a password that must be said before money gets transferred. Be safe. Not sorry.
As for the chicken thieves, may the vicious and biting fleas, of 1066 camels, invade their privates, for 750 years. And may they after all this, succumb to the bubonic plague, after spending 40 days in agony …..