Category: Must Read Articles
Understanding Cryptocurrency: The Basics
Are you intrigued by cryptocurrency but find it as perplexing as a cryptic crossword? Fear not! We’re here to guide you through this beginner-friendly exploration into the realm of digital currencies. It’s time to unravel the complexities of cryptocurrency and set you on a path to navigating this exciting digital landscape safely.
Mastering macOS: A Beginner’s Guide to Becoming a Power User
Apple’s macOS is lauded for its intuitive user interface, offering even the most novice users a comfortable and easy computing experience. However, beneath this user-friendly facade lies an extensive ecosystem of features and tools that, when properly utilized, can significantly enhance productivity and streamline workflows. This guide will serve as your roadmap in your journey to becoming a power user of the Mac, providing you with an in-depth look at the strategies and techniques you’ll need to harness the full potential of your Mac.
Mastering The Art Of Digital Communication in the Age of Remote Work
Once upon a time, interpersonal skills were associated primarily with face-to-face interactions. Fast forward to 2023, and the landscape has drastically changed. As remote work and digital communication tools aren’t going anywhere, the demand for individuals with robust interpersonal skills is sky-high. And why not? After all, no matter how advanced our machines get, they simply cannot replicate the lively, engaging, and instinctual nature of human communication perfectly.
Apple Officially Unveils Vision Pro VR Headset
At the annual worldwide developers conference WWDC, held in Cupertino, California, Apple CEO Tim Cook finally unveiled the long-awaited and highly speculated headset, known as “Vision Pro.”
Encryption: Why It Matters to You, Even If You Think You Have ‘Nothing to Hide
Have you ever wondered how your sensitive information stays secure when you’re shopping online or sending a private email? The answer lies in something called encryption, a complex system of coding that disguises your data to keep it safe from prying eyes. Some might argue, “I have nothing to hide. Why should I care about encryption?” Well, the truth is, encryption is critical for everyone, and here’s why.
The Critical Importance of Blue Light Filters: Protect Your Eyes and Circadian Rhythms
As the world becomes increasingly digital, many of us find ourselves spending hours in front of screens, whether for work or leisure. This prolonged exposure to electronic devices has sparked concerns about the impact of blue light on our eyes and overall well-being. In this article, we will explore the importance of using blue-light filters and discuss the science behind how they can help protect your eyes and maintain healthy circadian rhythms.
Digital Treasure Maps: Uncovering the Best Hidden Gems of the Internet
Ahoy, intrepid explorers of the digital realm! Today, we’re setting sail on a grand adventure to discover the hidden gems scattered throughout the vast ocean of the internet. We know that navigating these waters can sometimes be overwhelming, with countless websites, apps, and resources vying for our attention. But fear not, for we have charted a course that will lead you to some of the most intriguing, lesser-known digital treasures just waiting to be discovered. So, grab your virtual spyglass and let’s embark on this thrilling journey together!
A Brief Discourse on Discord
Ah, Discord. The platform that has taken the online gaming world by storm. But what exactly is it, and why should you care? Let’s take a dive into the basics of Discord, shall we? First and foremost, Discord is a communication platform. It allows people to chat, voice chat, and…
Framework Teases a Better Future For Laptop Computing
Framework’s newest upgrade is a serious nod to a future full of modular, open hardware. Let’s hope they follow through. Framework has announced the launch of the second-generation Framework Laptop, a device that is meant to be faster and more sturdy than its predecessor. More importantly, it signals Framework’s commitment…
What to Do if Your Amazon Order Never Arrives but They Say it Was Delivered
What should you do if Amazon says that your order was delivered but you never actually receive it? For the most part an Amazon delivery happens when they say it will. But sometimes an Amazon order will be marked as having been delivered even though the order has never been received by the person who ordered it. Here’s what to do if your order from Amazon hasn’t shown up even though Amazon says that it was delivered.
10 iPhone Tips for Blocking Out the *Hackers* During Holiday Travel
10 iPhone practices for blocking out the *hackers* during holiday travel this season. We can all agree that the holidays are cherished traditions, best spent with our family and friends. And for many folks, “family-time” means it’s traveling-time. Whether you enjoy the early morning hours at your local airport or…
Mac Pro Tips: How to install yabai and skhd
In our last post, we briefly went over yabai, which is a tiling window manager for macOS. If you’re not experienced with Linux systems, the concept of a window manager (WM) is likely foreign to you, so I’ll pause briefly to provide an explanation and definition of a window manager, specifically a “tiling” WM.
Mac Pro Tips: Window Management.
If you’re one of the many mac users who’s spending a significant amount of time on your computer, you’ve likely spent some time thinking about how to speed up your workflow.
How to Protect Yourself or Your Business from Ransomware in 2 Steps
The City of Baltimore had their city government computer system shut down by the Robbinhood ransomware. Yet it could have been avoided, or at least mitigated. Here’s how to protect yourself or a business from ransomware.
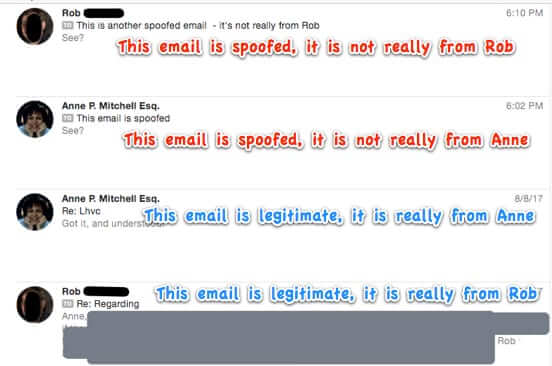
How Displaying Sender’s Contact Image and Info in Email Allows Scammers to Steal from You
Every webmail service out there, be it Gmail, Yahoo, Hotmail, or other, encourages you to upload or merge your contacts with their system. And most Mac and PC email programs automatically cross-reference an incoming email sender with their entry in your contacts. The result is often that their contact profile picture, and ‘friendly’ name, is displayed as the sender of that email in your inbox.