Tag: Security
Do I Have to Worry About the Spectre Intel Chip Security Flaw? And What is Speculative Execution?
As news of the Intel chip security flaw has started to permeate public awareness, people are asking themselves two main questions: “Do I have to worry about it, and if so what do I need to do?” and “Just what is speculative execution?” (The issue with the chips has to do with the speculative execution function.) This flaw is said to affect millions of Windows, Mac, and Linux computers around the world. “Major flaw in millions of Intel chips revealed” screams the BBC headline. “A Critical Intel Flaw Breaks Basic Security for Most Computers,” banners Wired. Even Popular Mechanics is getting in on it, stating that “Horrific Security Flaw Affects Decade of Intel Processors.” Although, others are starting to say that it’s not limited to Intel chips, as pointed out by the Axios story, “Massive chip flaw not limited to Intel.”
How GDPR Will Conflict with Almost Everything
I was recently interviewed, in my capacity as an Internet law and policy attorney, and head of the Institute for Social Internet Public Policy, for an article sponsored by RSA about the impact that GDPR (the EU’s General Data Protection Rules), which goes into effect in the European Union in May 2018, is going to impact, well, everything. And, in particular, about how it will impact U.S. based businesses, because, trust me, it will.
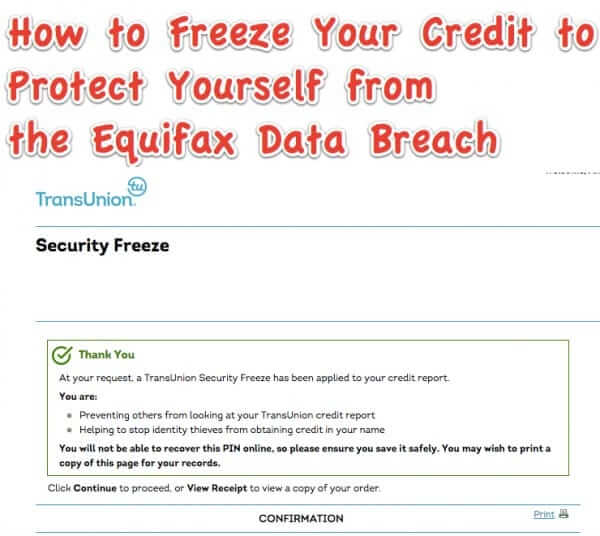
What YOU Need to do RIGHT NOW Because of the Equifax Data Breach in Order to Protect Yourself
Last week we started hearing about the Equifax data breach, although Equifax had actually known about the data breach at least a month earlier. (The full text of the Equifax statement about the cybersecurity data breach is reprinted below.) The most stunning thing about this breach is the breadth of it: the Personally Identifiable Information (PII), including names, social security numbers, and driver’s license numbers of 143 million U.S. citizens were exposed in this breach. Here is what you need to do, right now, to protect yourself.
The Internet Patrol Voted Top Security Blog by Credit Donkey
We here at the Internet Patrol are thrilled to have been voted a “top security blog” by Credit Donkey, which, while focusing primarily on making personal finance “donkey-proof” (by which they mean fun and easy to understand), also covers the online security sector.
What are Forged Cookie Attacks, and Why are They in the News?
There has been quite a bit in the news this week about “forged cookies” and “forged cookie attacks”, but little to actually explain them. A forged cookie attack is exactly what it sounds like though: a way for hackers to forge the information in your browser cookie, and when that information includes an authentication mechanism, voila! They can log into your account.
How to Install the Apple Security Update on Jailbroken Phones
You know you need to apply the urgent Apple security update on your jailbroken iPhone. While you can’t do it without restoring your iPhone to its unjailbroken state, it’s very easy to get the update installed and then rejailbreak your iPhone. Here’s our step-by-step tutorial for how to install the iOS security update on your jailbroken phone, with screenshots.
Adult Friend Finders, Cams.com and Penthouse Accounts Among Massive Hack and Data Leak
Those of you who breathed a sigh of relief over the hacking of the Ashley Madison adult cheaters site because instead you are on one of the Friend Finder sex hookup sites, such as Adult Friend Finder (AdultFriendFinder.com) – guess what? It turns out that last month Friend Finder Networks, parent company of Adult Friend Finder and other associated sites such as Penthouse.com, Cams.com, iCams.com, and Stripshow.com – totaling over 412 million accounts – was hacked, exposing email addresses, passwords, and IP addresses – everything your spouse or significant other needs to nail you nailing someone else.
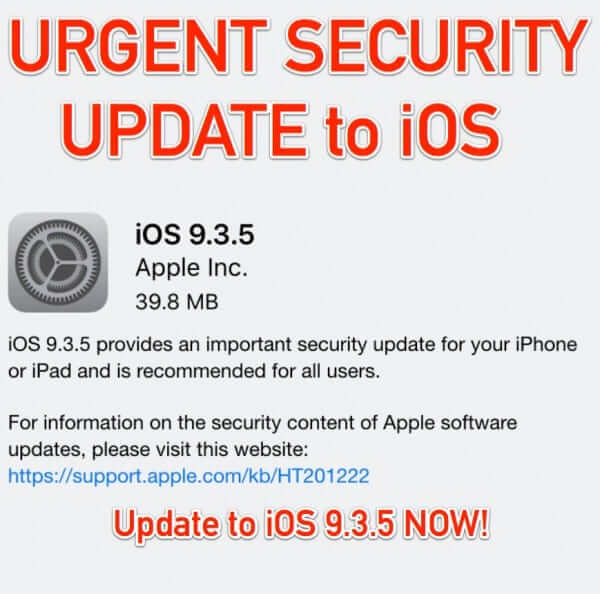
Urgent iOS 9.3.5 Security Update for iPhone, iPod and iPad
Yesterday Apple released an urgent security date for iOS, affecting all iOS devices, such as iPhone, iPad, and iPod. Security update 9.3.5 is essentially a security patch, to fix not one, but three different security holes that have been known to be exploited by spyware created by an American-owned Israeli group known as the NSO Group. NSO Group was acquired by San Francisco-based equity fund Francisco Partners in 2014.
Federal Agencies to Include Your Social Media Accounts in Security Clearance Background Check
We’ve been telling readers for years that you need to be very careful about what you say and post on social media, whether Facebook, Twitter, Snapchat, Instagram, or other sites. It can be used against you in divorce proceedings, in lawsuits and criminal trials, and, of course, in the court of popular opinion. Now add another place it can be used against you to the list: during the background check for your Federal security clearance. (Full text of directive below.)
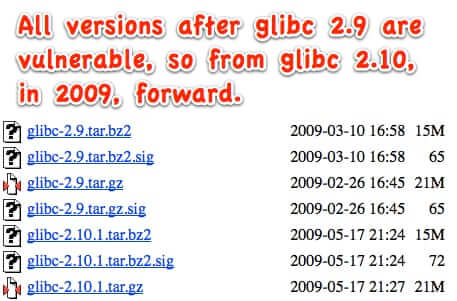
The getaddrinfo Vulnerability that Has Everyone Freaking Out Explained
By now you have probably heard about the enormous security flaw that was recently discovered that, experts say, left thousands of applications and devices vulnerable to remote attacks and control. It is a flaw that has been around since 2009, and has the potential to affect any server that is running any post-2008 version of the Gnu C open source library called glibc. It is the function getaddrinfo() within the glibc library that has the flaw, and it is so widely distributed that it is impossible to estimate just how many applications and hardware installs are running the flawed versions (of which there are at least 7 main version and dozens of incremental update versions).
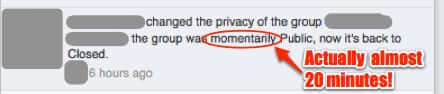
How Private are Facebook Private Closed Groups Really? Not Very it Turns Out
You know that old adage, that something is only as strong as its weakest link? Well, private Facebook groups are only as private as the admins keep them. Which means that all it takes is for one admin to accidentally (or intentionally) make the group public for a period of time, during which people who aren’t members of the closed Facebook group can see both the members, and what they posted. So how safe is it to rely on the private, closed status of a Facebook group? Not very, it turns out.
Ashley Madison Knew Security was Weak; Courts say Feds can go after Companies with Weak Security
Evidence in the form of leaked email demonstrates that Ashley Madison execs knew that their security was weak. A Federal court ruling last week says that the Federal Trade Commission (FTC) can go after companies whose Internet security is weak. Hrrm…
FitBit, Other Wearable Tracking Devices and Apps High Security Risk says Report
A new report released by Internet security firm Symantec highlights the security risks of personal and wearable tracking devices such as the FitBit, and even self-tracking apps such as Runkeeper, Runtastic, and MapMyRun. In our efforts to track and quantify our every move (what Symantec calls the “Quantified Self” movement), we are generating an unbelievable amount of data, including location data, that can be used to profile us, track our location, and even to steal our identity.
Smart Lightbulb Security Flaw Exposes Your Wifi Passwords
A lightbulb as a port of entry for a hacker to steal your wifi password? Yes! Specifically the LIFX smart lightbulbs, but it could be any smart bulb, or for that matter any other “smart” thing connected to that Internet of things.
Free Email Privacy and Security Tester
Email Privacy Tester is exactly what it says – a way to test your email program for privacy and security leaks. And it’s free!