Tag: Security
Report Highlights Scary New iOS Exploit via iMessage, Putting iPhone Security at Risk
Digital security firm Kaspersky has posted information about a recent cyberattack that targeted the iPhones of Kaspersky employees, which were infected with spyware that is part of a campaign the company dubbed, “Operation Triangulation.”
Navigating the Cyber Seas: Unmasking and Dodging the Latest Email Phishing Scams Like a Seasoned Mariner!
Ahoy, digital sailors! Today, we’re embarking on a thrilling voyage to navigate the treacherous waters of the internet. Our mission? To help you, our dear readers, spot and avoid the latest phishing scams that are swimming around in your email inbox, just waiting to take a bite out of your…
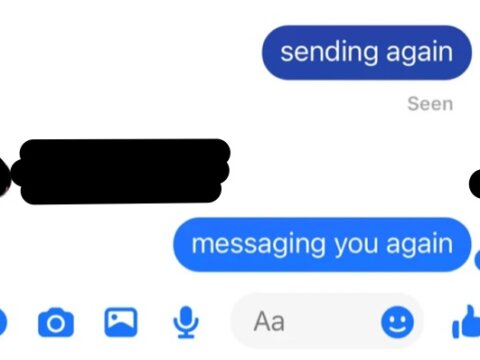
Facebook Messenger Read Receipts Huge Risk for the Abused, Bullied and Stalked
Facebook enables abusers. And they know that they do it. In a world full of online stalking, cyber bullying, and intimidation of the abused and traumatized, the fact that Facebook has never given users the ability to turn off Facebook Messenger read receipts may be one of the most egregious hand-offs of power to abusers ever to be perpetrated by a social media platform.
Google Paying $29.5 Million To Settle Lawsuits Over User Location Tracking
Google has agreed to pay a total of $29.5 million to settle two lawsuits regarding the company’s geographic tracking of their users.
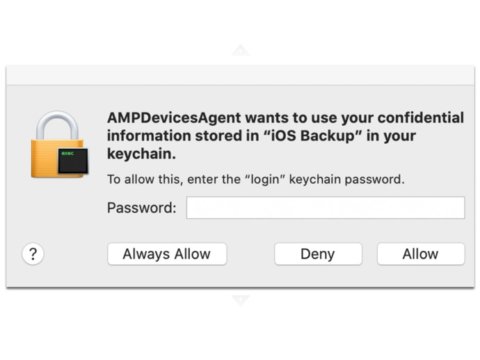
Here’s What ‘AmpDevicesAgent Wants to Use Your Confidential Information’ Means
“AMPDevicesAgent wants to use your confidential information stored in iOS backup in your keychain” screams the intrusive popup, over and over no matter how many times you tell it “Deny”. Given the relative lack of information provided, and given that the scant information that is provided includes the ominous word “confidential”, of the three choices offered to satisfy the popup, which are ‘allow’ (no), ‘always allow’ (heck no), and ‘deny’ (yes, that one), that last option (‘deny’) should be your default, or even knee-jerk, reaction, especially as the other two options require you to enter your password (eek). At least until you can figure out what the heck it all means.
Animoto Says Breached Passwords were Encrypted so Why do the Hackers Have My Full Password?
Last summer Animoto was the target of a data breach, in their posted-but-not-emailed announcement of the breach Animoto assured users that any compromised passwords had been “hashed and salted”. And yet, blackmail spammers now have full Animoto passwords.
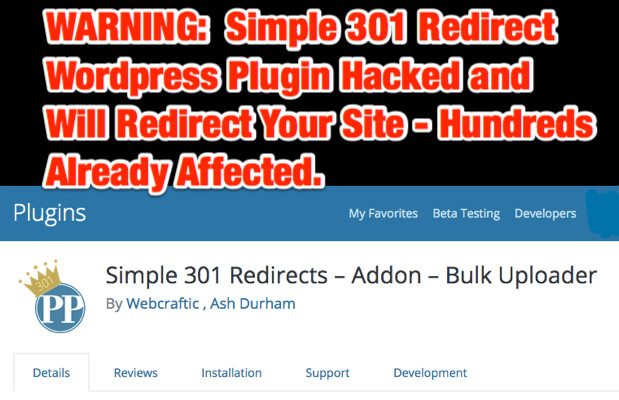
WARNING: Simple 301 Redirect WordPress Plugin Hacked and Will Redirect Your Site – Hundreds Already Affected
If you run the Wordpress plugin Simple 301 Redirect plugin, or the 301 Redirect addon Bulk Uploader by Webcraftic and Ash Durham, you are in danger of having your site get redirected to a malicious site.
ZombieLoad, Meltdown and Spectre: Triple Threat to Nearly All Computers
Zombie Load, Spectre, and Meltdown are security holes in the processors of many, many personal computers as well as servers, including those in the cloud.
How to Protect Yourself or Your Business from Ransomware in 2 Steps
The City of Baltimore had their city government computer system shut down by the Robbinhood ransomware. Yet it could have been avoided, or at least mitigated. Here’s how to protect yourself or a business from ransomware.
Tesla: Data Security Hell on Wheels?
The same data uploads and downloads that make Teslas dream cars for some Tesla owners also may make them security hell for all Tesla drivers. That’s because Tesla vehicles are big, wheeled Internet of Things devices.
Google Slipped an Undisclosed Microphone into Your Nest Security System
It all started with a seemingly innocent Google blog post earlier this month, in which Google announced that their ‘Hey Google’ Google Assistant was ready to go live on Nest Secure Nest Guard home security devices. Then people started having that ‘waaaait a minute…’ moment: this meant that there had to be a microphone in that Nest Guard device.
Data Breach at the Post Office: USPS Informed Delivery Service Database Exposes Data of 60million Users
Last year (in fact almost a year ago exactly) we told you about the U.S. Post Office’s new ‘Informed Delivery’ service. For those of you not familiar with the USPS Informed Delivery service, well, count your blessings. Because the postal service has experienced a serious breach, making the personal information of all 60 million plus Informed Delivery vulnerable.
Colorado Second State to Enact New Consumer Data Protection Law in 90 Days
Hot on the heels of California passing their California Consumer Protection Act (CCPA) which is actually a consumer data protection law, and on the slightly more distant heels of the passage and enactment of the General Data Protection Regulation (GDPR), Colorado has both passed and enacted the Colorado Consumer Data Protection Act (CCDPA).
Reddit Announces ‘Security Incident’
Reddit experienced a “security incident” in June, which they announced by email this month (August, 2018). While an email to Reddit users says that the hack affected “account credentials from 2007”, the full story paints a substantially broader picture.
My Friend Cayla Doll, Other Toys, Hackers’ Delight and Parents’ Nightmare
If your child, or someone you know, received a My Friend Cayla doll, a Furby Connect doll, a Q50 children’s smartwatch, or a Sphero BB-8 droid (or quite likely one of a number of other toys or devices aimed at children, and that connect to the Internet via Bluetooth), that device – and thus the child who plays with it or uses it – is at risk of being hacked, personal data stolen, and even a hacker talking to the child, all because of unsecure Bluetooth connections.