
Memes. They’re cute. They’re funny. And they’re infected. That’s what researchers are saying about memes posted on Twitter from a particular account. The memes had commands embedded in their code, so that to look at the meme it looked normal, but when a computer infected with the particular malware encountered the meme, it would read the command and then execute it.
For example the code “/print” was embedded in the memes, which would cause the infected computer to take a screenshot.
In explaining the malicious memes, Hacker News said “Besides taking screenshots, the malware can also be given a variety of other commands, such as to retrieve a list of running processes, grab the account name of the logged in user, get filenames from specific directories on an infected machine, and grab a dump of the user’s clipboard.”
Commands that were discovered in the memes include /print (does a screen capture), /processos (retrieves a list of the processes running on the infected computer), /clip (grabs the contents from the computer’s clipboard), /username (grabs the username from the infected computer), and /docs which retrieves files.
Once the computer executed the commands, it would pass the results back to the bad guys.
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.
The technique of hiding malicious content within the code of a digital image is known as steganography. Steganography has been around, and used by cyber criminals, for a while, however using it in this way – to embed commands in an image on social media, and to have the infected computers call home to the images in a particular Twitter account to get their orders, is new.
Said the researchers who discovered it, “This new threat is notable because the malware’s commands are received via a legitimate service (which is also a popular social networking platform), employs the use of benign-looking yet malicious memes, and it cannot be taken down unless the malicious Twitter account is disabled.”
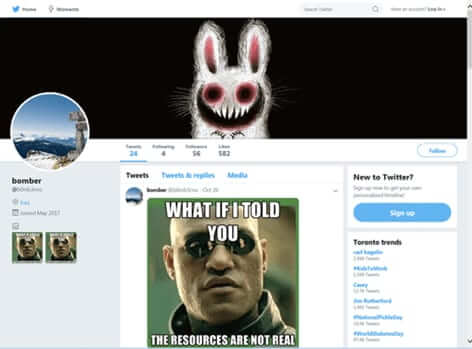
The Twitter Account that was Posting the Malicious Memes
The malware that is running on the computers, christened TROJAN.MSIL.BERBOMTHUM.AA by researchers, is Windows malware. Once a PC is infected with TROJAN.MSIL.BERBOMTHUM.AA, it can read the hidden code in the memes, and then execute the commands contained within the meme.
The good news is that the infected memes were coming from one particular Twitter account, which Twitter has now shut down, and at the time there were only two such memes in the account, which were posted in October.
The bad news is that you can certainly expect more of this sort of exploit. And by having one component of their scheme resident on a public platform like Twitter, the bad guys have the advantage that nobody is going to shut Twitter down, like they would a private malware server.
If you think that your computer may have become infected, there are [destination content has been removed at other end :~( ]
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.










What’s a Twiitter meme?