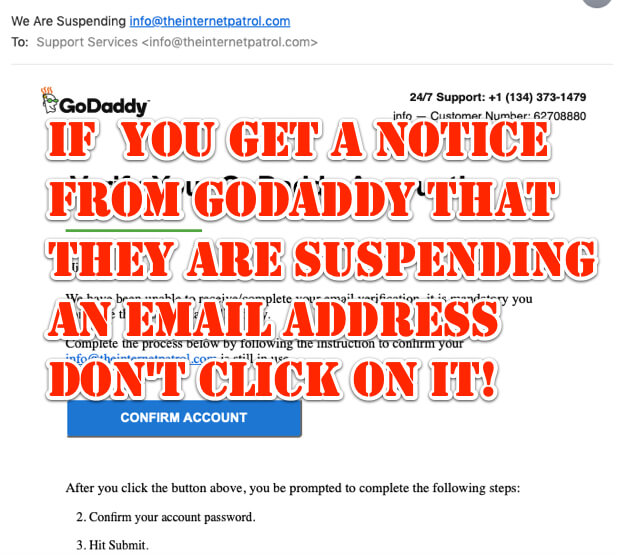
If you receive an email like the one below from GoDaddy saying that they are suspending your email address and that you need to verify your account, don’t click on it! It’s a scam, and likely to download malware onto your computer or device!
It really looks as if it could be from GoDaddy, including because they stole GoDaddy’s logo and put it in their fake email. All of this is intended to lull you into a false sense of security, and to believe that the email really is from GoDaddy. (Read our article here about how having your email program display senders’ images and info helps scammers.)
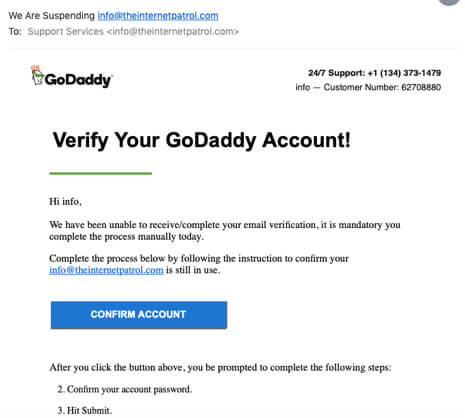
The text of the fraudulent email says “Verify Your GoDaddy Account! Hi (your name), We have been unable to receive/complete your email verification, it is mandatory you complete the process manually today.Complete the process below by following the instruction to confirm your (your email address) is still in use. After you click the button above, you be prompted to complete the following steps:2. Confirm your account password. 3. Hit Submit.”
Now, depending on how your email program works and is set, you may be able to notice that even though the name in the ‘From:’ address says ‘GoDaddy’, the email address itself will look something like this:
“HamishPorteous.rhyta.AmeliaPenfold.teleworm@vestedop.com”
Decidedly not a GoDaddy address.
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.
And, in fact, the full headers of this scam email look like this:
To: Support Services
Arc-Seal: i=1; a=rsa-sha256; t=1576602310; cv=none; d=google.com; s=arc-20160816; b=kCUtQP2NqSKaxr4jt2S8PpTL4/HKMbyplUa6O55BVjU/t8ei5xQkOVQzcovd1aIKx4 uvc6+OHBHL4og4jRoTcZyy952l2GLD8RyAwDXLggOvFqK/3cIjC99VymHzOgcqhWYjL2 mksG3yBBmiFEz8Y0F2rR8pclGns/OGReb5Q15wV+xXxyyT0NxHgZJrDVdSpartCKBNUs uZEyPzNF15qzwAtLQxaUge7xs5XBLt2ypjcEI7KbTPS9+vXZw7VV9uYBE/94buB1CyOQ lyU4ZWH8VQi+3lZ7An150sMNZiVDvmv2NjtXq8nMieFvEOMquj/k5z3QhfJAMmPzwOO8 XBRg==
X-Ovh-Tracer-Id: 773774714898621493
X-Received: by 2002:a17:902:7c83:: with SMTP id y3mr24121792pll.34.1576602311148; Tue, 17 Dec 2019 09:05:11 -0800 (PST)
X-Received: by 2002:a17:902:7c83:: with SMTP id y3mr24121684pll.34.1576602310117; Tue, 17 Dec 2019 09:05:10 -0800 (PST)
Return-Path: (SRS0=LV7g=2H=vestedop.com=hamishporteous.rhyta.ameliapenfold.teleworm@bounce.secureserver.net)
Arc-Authentication-Results: i=1; mx.google.com; spf=fail (google.com: domain of srs0=lv7g=2h=vestedop.com=hamishporteous.rhyta.ameliapenfold.teleworm@bounce.secureserver.net does not designate 69.12.213.130 as permitted sender) smtp.mailfrom=”SRS0=LV7g=2H=vestedop.com=hamishporteous.rhyta.ameliapenfold.teleworm@bounce.secureserver.net”
X-Originating-Ip: [40.115.181.175]
X-Vr-Spamscore: 20
X-Google-Smtp-Source: APXvYqwlJYu0apPlWvj7nv3V2vcdy4vOJDIq4MrFY1STKk5uEYgqW9E78eoE6XoMmm48SQkfJGq2
X-Virus-Scanned: Content scanner at isipp.com
Mime-Version: 1.0
Authentication-Results: mx.google.com; spf=fail (google.com: domain of srs0=lv7g=2h=vestedop.com=hamishporteous.rhyta.ameliapenfold.teleworm@bounce.secureserver.net does not designate 69.12.213.130 as permitted sender) smtp.mailfrom=”SRS0=LV7g=2H=vestedop.com=hamishporteous.rhyta.ameliapenfold.teleworm@bounce.secureserver.net”
X-Priority: 1 (Highest)
Arc-Message-Signature: i=1; a=rsa-sha256; c=relaxed/relaxed; d=google.com; s=arc-20160816; h=mime-version:date:content-transfer-encoding:importance:message-id :subject:to:from:delivered-to; bh=Xjg5Xr8aVBMpY4DQoy3SZtf9hB4LZ2PJ6thbPyGRP6M=; b=nUUCf0trG+h9JbQWSfF9+jraS4cDhS6JFthZkhLY6ALtpnHSD752HY3wKlPCLkcIXj VSYdSpGfO+bTihrlReP2QjOZIWG8b/9fj6KdaZ05UTKGJFYUYBm7T7y7J07K6lMjj/3u nKpWVouPWwP/z5RLXW7Z75FIEp1Hk8MIxaDe3VfhQQS9ln4Dk2sqZhQOde5pKS4it7j+ 96lMgma2Regt7apw9ijCk7GtqcUBSPrcjXaNC8ztPZ0VNJvN69SR5Vyodat91jRmzrLD pN/wAxT0IEXD8b+ce/e2OqzieXegf7paINdCuaWWjmuUzuqENFfZSmZO/QUmkpxAgg/N 9n3g==
(bffef878-13ce-9eb7-fcc9-727626ab5a65@vestedop.com)
Content-Transfer-Encoding: quoted-printable
X-Cmae-Envelope: MS4wfHOpZKrlZWTYFrOAghBPaJAkFjrEov+wdx9EH8ii006woRa5sJoRyELp5UTH32wP55XsyT8rGyp88s0i003uoR7P10CUcrfPnrujYoCfy9NPL1e5gLC0 frLfkjJ4D8KLdM8IARHnS/IvgQgnIleC6cHrfZ6hXZskMe2GPlR55Nf9AONIEvGRxAYKMh3HuWrFmlzdJo2fxZE3M3GuaKgjl8nvMeVY46SIKmNxw4TC/Mdh 0k9wWT4X97PMubtaDVAQqg==
X-Clientproxiedby: EX2.indiv.local (172.16.6.2) To EX1.indiv.local (172.16.6.1)
Importance: High
Content-Type: text/html; charset=”utf-8″
Received-Spf: fail (google.com: domain of srs0=lv7g=2h=vestedop.com=hamishporteous.rhyta.ameliapenfold.teleworm@bounce.secureserver.net does not designate 69.12.213.130 as permitted sender) client-ip=69.12.213.130;
Delivered-To: (our email address)
X-Vr-Spamstate: OK
Received: by 2002:a05:6214:ab1:0:0:0:0 with SMTP id ew17csp2971187qvb; Tue, 17 Dec 2019 09:09:12 -0800 (PST)
([68.178.213.10]) (envelope-sender hamishporteous.rhyta.ameliapenfold.teleworm@vestedop.com) by p3plsmtp27-02-25.prod.phx3.secureserver.net (qmail-1.03) with SMTP for
Received: from mo1-4.mail-out.ovh.ca ([198.100.159.120]) (using TLSv1.2 with cipher ECDHE-RSA-AES256-GCM-SHA384 256/256 bits) (Client did not present a certificate) by CMGW with ESMTP id hGHOiYEp8H1uqhGHPiFLdI; Tue, 17 Dec 2019 10:05:03 -0700
Received: from EX1.indiv.local (gw1.ex.mail.ovh.ca [192.95.3.8]) by mo1.mail-out.ovh.ca (Postfix) with ESMTPS id E576385993 for
Received: from [127.0.0.1] (40.115.181.175) by EX1.indiv.local (172.16.6.1) with Microsoft SMTP Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256) id 15.1.1847.3; Tue, 17 Dec 2019 12:04:55 -0500
In case you are not familiar with reading email headers, we have a plain English explanation of them in our how to report spam tutorial.
What these email headers tell us is that this email came not from GoDaddy’s email servers, but was sent by someone using a Microsoft product, sent through OVH.ca. OVH is a cloud service headquartered in France (OVH stands for On Vous Héberge, which translates to We Host You), and OVH.ca is their Canadian domain address.
So, there are many clues that this is not really from GoDaddy, and is a spoofed scam, but only if you know how and where to look.
Did you receive one of these scam emails “from” GoDaddy?
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.










Hopefully, folks who know who / what GoDaddy actually is would automatically know how to “read a URL”, but you perform a very valuable service in suggesting that everyone is smart enough to learn to — and should always — read every URL before clicking — in all emails or all websites fake or real. (thanks, I feel better now).