A newly announced exploitable security weakness in the WPA2 protocol is spelling trouble for most Internet wi-fi routers, including home routers, and Internet of Things (IoT) devices. The KRACK (Key Reinstallation Attacks) vulnerability in WPA2 has the potential for such widespread security incidents (because WPA2 is deployed nearly everywhere, and because this is not OS-specific, but attacks the router) that the revealing of it was coordinated among the researchers who have discovered it.
WPA2, which stands for “Wi-Fi Protected Access II”, is widely deployed as the default security protocol in routers and devices that are attached to the Internet, such as Internet of Things appliances and devices.
A Home Router Offering Only WPA2 Security Options
Once the bad guys exploit the KRACK vulnerability and connect to your router, IoT device, etc., they are able to essentially eavesdrop on all of your internet traffic including passwords, banking details, etc., which they can now decrypt.
Remember, this vulnerability is resident on your router (among other things), through which most of your Internet traffic is, well, routed.
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.
In the disclosure security researcher Mathy Vanhoef and colleagues explain:
We discovered serious weaknesses in WPA2, a protocol that secures all modern protected Wi-Fi networks. An attacker within range of a victim can exploit these weaknesses using key reinstallation attacks (KRACKs). Concretely, attackers can use this novel attack technique to read information that was previously assumed to be safely encrypted. This can be abused to steal sensitive information such as credit card numbers, passwords, chat messages, emails, photos, and so on. The attack works against all modern protected Wi-Fi networks. Depending on the network configuration, it is also possible to inject and manipulate data. For example, an attacker might be able to inject ransomware or other malware into websites.
They go on to say that “The weaknesses are in the Wi-Fi standard itself, and not in individual products or implementations. Therefore, any correct implementation of WPA2 is likely affected. To prevent the attack, users must update affected products as soon as security updates become available. Note that if your device supports Wi-Fi, it is most likely affected. During our initial research, we discovered ourselves that Android, Linux, Apple, Windows, OpenBSD, MediaTek, Linksys, and others, are all affected by some variant of the attacks.”
The way that an attack against this vulnerability works is the bad guy has his client connect to the vulnerable server, and during the ‘handshake’ (when the server and the connecting client have their initial authentication exchange) the bad guy is able to cause the attacked WiFi device to reinstall an encryption key, which in turn causes it to reset the nonce*.
*In the Internet security/cryptography context, a ‘nonce’ refers to an arbitrary number that should only be used once. It is issued during the authentication handshake.
According to an article in ArsTechnica, “Both Windows and iOS aren’t believed to be vulnerable to the most effective attacks. Linux and Android appear to be more susceptible, because attackers can force network decryption on clients in seconds with little effort.”
Note that they say Windows and iOS aren’t believed to be vulnerable against the “most effective” attacks, not that they aren’t vulnerable (they are). Again, the researchers make a point of saying that “During our initial research, we discovered ourselves that Android, Linux, Apple, Windows, OpenBSD, MediaTek, Linksys, and others, are all affected by some variant of the attacks.”
Because this has now been announced, even if bad guys weren’t aware of it before and exploiting it already, they will be now. (This is why the research was kept so quiet, and the revealing of the exploit coordinated, so that the Internet security community – and end users – could rush to patch it as quickly as possible before the bad guys are able to abuse it).
So what should you do about this?
What to Do About the KRACK Vulnerability in WPA2
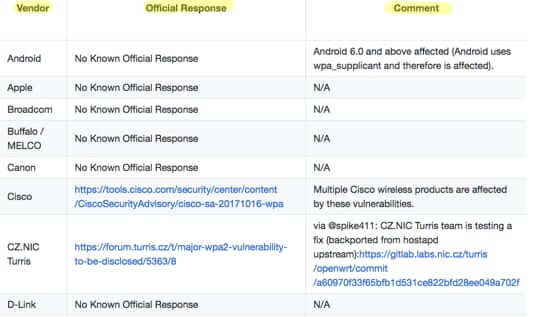
First, check this GitHub page which is tracking vendor response to KRACK, which includes links to patches and updates by vendor, as they are made available.
Second, do not go to websites that don’t offer HTTPS. Although HTTPS is not a guarantee that you won’t end up affected by this, it does offer additional protection as compared to non-HTTPS (i.e. HTTP only) sites. As the KRACK researchers explain, “Although websites or apps may use HTTPS as an additional layer of protection, we warn that this extra protection can (still) be bypassed in a worrying number of situations. For example, HTTPS was previously bypassed in non-browser software, in Apple’s iOS and OS X, in Android apps, in Android apps again, in banking apps, and even in VPN apps.”
So, again, HTTPS isn’t a magic bullet, but it is less ‘wide open’ than sites which do not offer it.
Finally, when you are out and about, if you have the option to tether your computer through your phone, rather than connecting to a public WiFi network, it’s a good idea to do so.
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.










Thank you for this important information. dennis