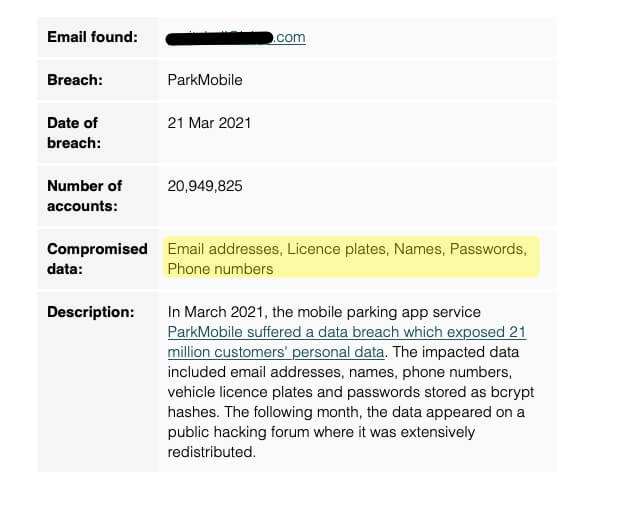
On March 31, 2021, ParkMobile experienced a signification data breach. By significant we mean that nearly 21million accounts were breached (20,949,825, to be exact). And by data breach, we mean the data of all of their users, which data includes (but is not necessarily limited to) both the usual (names, phone numbers, and email addresses) and the slightly less usual: passwords and license plate numbers.
It saddens us to have to report on this, because heretofore we have been big fans of ParkMobile, observing that “you will love the ‘pay by phone parking’ mobile parking meter app ParkMobile”, and even publishing a complete (at the time) list of ParkMobile zones offering the ParkMobile option.
While the breach was first widely reported in the security communities a bit over two weeks ago, the breach actually happened more than 6 weeks ago. ParkMobile did issue a brief announcement of the breach, on March 26th, but all that it said was “We recently became aware of a cybersecurity incident linked to a vulnerability in a third-party software that we use. In response, we immediately launched an investigation with the assistance of a leading cybersecurity firm to address the incident. Out of an abundance of caution, we have also notified the appropriate law enforcement authorities.” There was another paragraph that indicated what the hackers hadn’t managed to get (credit card information) but that didn’t mention anything that the hackers had managed to extract (like license plate numbers, and passwords).
Then, a bit over two weeks later, ParkMobile updated the statement, saying that the passwords had been encrypted, and that “Our investigation has confirmed that basic user information – license plate numbers and, if provided by the user, email addresses and/or phone numbers, and vehicle nicknames – was accessed. In a small percentage of cases, mailing addresses were affected. No credit cards or parking transaction history were accessed, and we do not collect Social Security numbers, driver’s license numbers, or dates of birth.”
And yet, there seems to have been little effort to make sure that ParkMobile users were made aware of the issue and, in fact, the way that it came to more public attention was that security researcher Brian Krebs, who write and runs Krebs on Security, is himself a ParkMobile user (or at least was), and he in turn was advised by colleagues at Gemini Advisory (a cyber-threat intelligence outfit), who told Krebs that in a Russian forum a database of hacked data from ParkMobile was being offered for sale for $125,000, and that Krebs’ own ParkMobile account was one of the hacked accounts, and that the data from his account included his email address, telephone number, and license plate numbers for all four of the vehicles with which he and his family had used ParkMobile.
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.
Not only did Krebs have to learn of this breach of his data from a third party (much like you may be doing by reading this right now) rather than directly from ParkMobile but, Krebs points out, “It’s also curious that ParkMobile hasn’t asked or forced its users to change their passwords as a precautionary measure.” Indeed.
One reason that ParkMobile may have erred (and we do mean erred) on the side of not making a more public statement about the breach may be because the breach came almost immediately after ParkMobile announced that Europe-based EasyPark had voiced an intent to acquire ParkMobile. ParkMobile had announced that on the 9th of March and, curiously (or perhaps not) there has been nothing about a pending acquisition since.
Anyways, if you do use the ParkMobile app, be sure to change your password!
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.










I await with eager interest the internet patrol analysis of WHY these breaches continue and what particular measures — technical and other — would stop them (maybe … executing CEOs? at half time in the Super Bowl?)?