
Last summer Animoto was the target of a data breach. In their posted-but-not-emailed announcement of the breach Animoto assured users that any compromised passwords had been “hashed and salted” (why am I suddenly hungry?)
However, they also added that “it’s unclear whether or not the key was accessed.”
Well, I have news for them: the key was accessed. Either that, or the passwords weren’t actually encrypted (hashed and salted), or the hackers found some other way to decrypt the passwords.
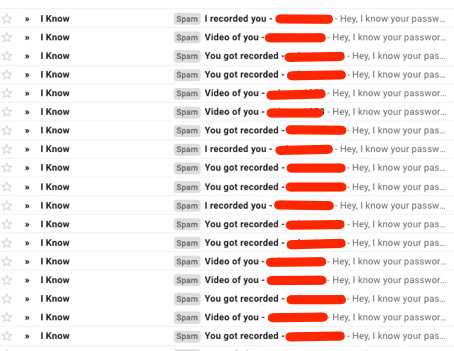
How do I know? Because this morning I woke up to 40 emails with some variation of this (and still counting):
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.
Do you see each of those red lines? Behind each one is my actual, correct Animoto password. Not “hashed and salted” – my actual password, completely unencrypted.
And as if that is not shocking enough, this was the first that I had heard about this breach, which occurred over a year ago! I (and who knows who-all else) was never notified by Animoto about the breach!
It wasn’t until I started investigating the spam that curiously contained my full, actual Animoto password that I discovered the “Important Security Announcement” on their website (which apparently was never emailed to .. you know .. their users who were impacted – at least not all of their users).
This “Important Security Announcement” is quoted below. The particularly relevant language is bolded for ease of reading.
Important Security Announcement
Beginning on August 16, 2018, Animoto began notifying its users about an issue that may involve their Animoto account information. We value our users’ privacy and, therefore, we want to provide the following details about the event, what data was involved, and the steps we’re taking to protect Animoto’s users’ information.
What Happened? On July 10, 2018, we received an alert of unusual activity on our system. We immediately stopped all suspicious activity and launched an investigation with the support of outside forensics experts. On August 6, 2018, we confirmed that the activity was unauthorized, and that user data may have been obtained. While we cannot confirm that data was removed from our systems or that any specific user’s information was affected, we wanted to let all our users know about this incident out of an abundance of caution.
What Information Was Involved? We determined that, as a result of the activity, data was accessed on July 10, 2018. The data may have included first name, last name, username (email address), hashed and salted passwords, geolocation, gender, and date of birth. While the passwords were hashed and salted (a method used to secure passwords with a key), it’s unclear whether or not the key was accessed. Complete payment card data was stored in a separate system and was not accessed. To date, Animoto has no evidence of any actual or attempted fraudulent misuse of information as a result of this incident.
What We Are Doing. We take this event, and the security of our users’ information, very seriously. We are reviewing our policies and procedures to better protect against an event like this from happening again in the future. In addition to working with third-party experts to conduct an investigation, we have notified law enforcement authorities and we continue to monitor for suspicious activity. We are examining ways to enhance overall network cyber threat detection at Animoto and continue to make enhancements to our systems to detect and prevent unauthorized access to user information, including rebuilding our infrastructure to make to it more secure.
What You Can Do. As an immediate precaution, we suggest all users change their Animoto passwords. If a user has the same or a similar password for other online accounts or email, we recommend users change those passwords or take other appropriate steps to protect those accounts or email addresses as well.
(From https://help.animoto.com/hc/en-us/articles/360008114514-Important-Security-Announcement)
###
But wait, there’s more.
I just an hour ago, while writing this article more than a year after the breach, logged into the Animoto website – using that same password. That’s right, not only had Animoto not taken the now-standard precaution of changing all passwords and requiring users to get a password reset in order to log in, but there was not even a notification of the issue when I logged in!
If I hadn’t been alerted to the issue by the blackmail efforts of the spammer, showing that they had my password, I would never have known that there was an issue at all, even after logging in to my compromised Animoto account.
Of course, upon logging in to my Animoto account this morning I immediately tried to cancel it; after all, I don’t want to be associated with any company or service that is so lax about the security of my personal information – but hey, there isn’t any easy way to cancel your account. You have to email them asking them to do it, and even that isn’t obvious from the site.
Bad Animoto, bad.
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.










Encryption is completely different from hashing, FYI. Passwords are generally stored as hashes. Hashing is impossible to reverse. It is possible, however, to compare the stored hashes to lists of “known” password hashes, so more common passwords may be easy to compare and match. Salting means ‘mixing in’ another component to each password hash, so that hashes between sites won’t match, even for the same password. However, if they are able to steal or determine the salt, it may still be possible implement that into their “cracking”.