Tag: flaw
Do I Have to Worry About the Spectre Intel Chip Security Flaw? And What is Speculative Execution?
As news of the Intel chip security flaw has started to permeate public awareness, people are asking themselves two main questions: “Do I have to worry about it, and if so what do I need to do?” and “Just what is speculative execution?” (The issue with the chips has to do with the speculative execution function.) This flaw is said to affect millions of Windows, Mac, and Linux computers around the world. “Major flaw in millions of Intel chips revealed” screams the BBC headline. “A Critical Intel Flaw Breaks Basic Security for Most Computers,” banners Wired. Even Popular Mechanics is getting in on it, stating that “Horrific Security Flaw Affects Decade of Intel Processors.” Although, others are starting to say that it’s not limited to Intel chips, as pointed out by the Axios story, “Massive chip flaw not limited to Intel.”
The getaddrinfo Vulnerability that Has Everyone Freaking Out Explained
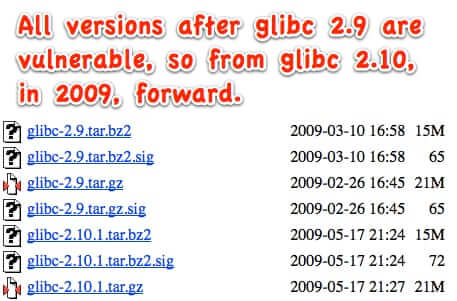
By now you have probably heard about the enormous security flaw that was recently discovered that, experts say, left thousands of applications and devices vulnerable to remote attacks and control. It is a flaw that has been around since 2009, and has the potential to affect any server that is running any post-2008 version of the Gnu C open source library called glibc. It is the function getaddrinfo() within the glibc library that has the flaw, and it is so widely distributed that it is impossible to estimate just how many applications and hardware installs are running the flawed versions (of which there are at least 7 main version and dozens of incremental update versions).
Millions of Iphones and iPads at Risk as Apple Rushes Security Update
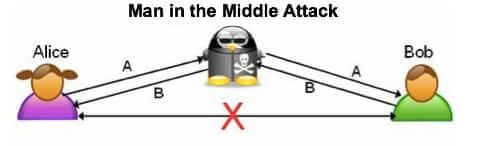
Apple has released a critical security update for iPhone and iPad iOS 7 and iOS 6. This urgent update is to fix the critical security vulnerability that exposes your data (including usernames, passwords, and other account credentials at nearly any website or service) to a “Man in the Middle” (MitM) attack.
Massive Android Security Hole Affects up to 99% of All Android Users
Three researchers in Germany at the University of Ulm have discovered a massive security hole in Android – so big, in fact, that it affects at least 97%, and as many as 99%, of all Android users. The researchers, Bastian Könings, Jens Nickels, and Florian Schaub, have discovered that the security flaw allows anyone who is sniffing around your connection on an unsecured wireless network to acquire your Google authorization credentials from a specific token (the authToken), giving them access to your contacts, your calendar and, well – really any application that authenticates you by using your Google authorization credentials contained within that authToken.
Apple Admits Problem with Apple iPhone 4.0 Reception, Sort Of
In a letter posted on the Apple website on Friday, just as everyone was leaving for the long weekend (we’re sure the timing is just coincidence), Apple admits that there is a bonafide Apple iPhone 4 reception problem. Well, sort of. What they really say is that the problem isn’t with the reception, or even with a faulty antenna – it’s with saying you have more bars of reception than you really do. Hrrm… way to shift the blame over to AT and T!