Tag: hackers
Hacking Crew Exploits Hidden Tech to Breach Prominent Companies
Researchers Sound the Alarm as Extortionists Target Victims Using File-Transfer Software
Microsoft Admits Breach, Hackers Accessed Users’ Outlook, Hotmail, and MSN Email for Months (Full Text of Microsoft Email Statement Included)
Microsoft has disclosed, over the weekend, that hackers have hacked into and accessed Microsoft users’ Outlook email, Hotmail email, and MSN email, over the course of several months, ending just last month (March of 2019).
My Friend Cayla Doll, Other Toys, Hackers’ Delight and Parents’ Nightmare
If your child, or someone you know, received a My Friend Cayla doll, a Furby Connect doll, a Q50 children’s smartwatch, or a Sphero BB-8 droid (or quite likely one of a number of other toys or devices aimed at children, and that connect to the Internet via Bluetooth), that device – and thus the child who plays with it or uses it – is at risk of being hacked, personal data stolen, and even a hacker talking to the child, all because of unsecure Bluetooth connections.
VTech Toy Hacker Gets Personal Information of Over 6million Children
You’ll need to pardon our rant, and if you are easily offended, you may want to skip this article. Because we want to know who the hell lets their kids register their personal information, including home address, pictures, and other personally identifying information or – even more mind-boggling – registers this information for their kids, online?
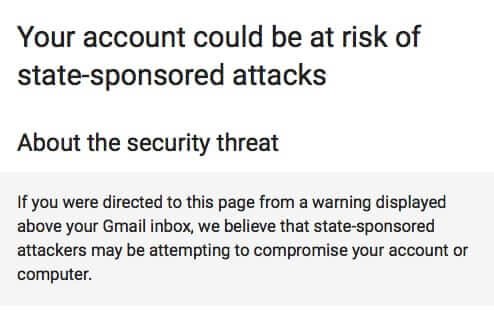
About Gmail’s “Warning: We believe state-sponsored attackers may be attempting to compromise your account or computer” Message
Did you get a message recently across the top of your Gmail account that says “Warning: We believe state-sponsored attackers may be attempting to compromise your account or computer. Protect yourself now”? Worried that someone may have hacked your Google or Gmail account? Read on…
ISIS Calls Anonymous ‘Idiots’ as Anonymous Declares War on ISIS
The hacker group known as Anonymous has declared cyber war on ISIS (the Islamic State, which also goes by ISIL and Daesh). While Anonymous has actually stated this previously, they have stepped up their game, and their public announcements of this war on ISIS, following last Friday’s attacks in Paris. In response to the announcement, ISIS released their own statement, calling Anonymous “idiots”.
Government Personnel Data Breach Included 5.6 Million Fingerprint Records
In June the U.S. Office of Personnel Management (OPM) revealed that there had been a massive security breach, exposing the personal personnel data of at least 21.5 million government employees. The data included social security numbers, names, and clearance information. What was less well known is that the data also included fingerprint records, and this week it has been revealed that the hackers got 5.6 million fingerprints.
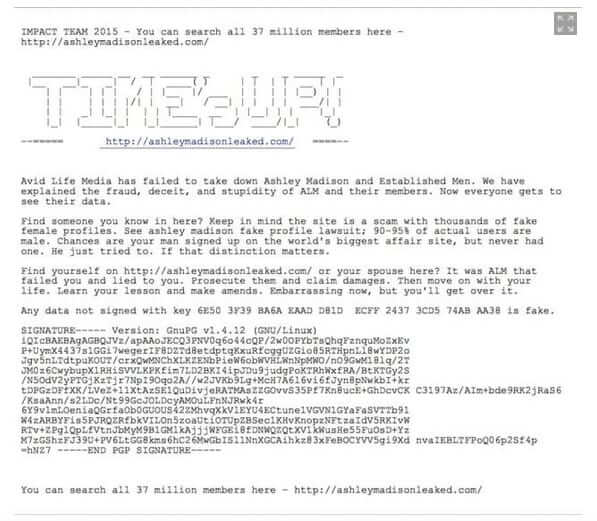
Update on Ashley Madison Hack and Data Dump
As we told our readers last month, the ‘have an affair and cheat on your spouse’ website Ashley Madison was hacked, and information on their “37,765,000 anonymous users” was grabbed by the hackers, who call themselves The Impact Team. Now the Impact Team has dumped and revealed all of the data online, and many people are worrying “Is my email address in the Ashley Madison data?”
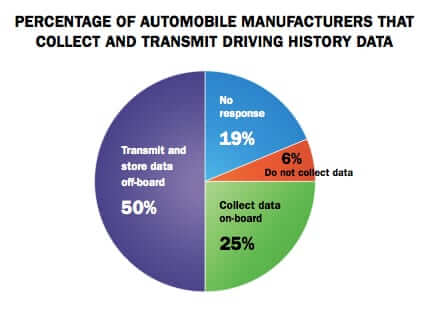
About the Jeep Hack and Hackers Hacking Cars and What to Do About It
By now you’ve probably heard about Andy Greenberg’s expose in Wired about driving a Jeep while hackers – wireless carjackers – hacked into it. Of course, Internet Patrol readers who read our Can Your Car Be Hacked Through its Onboard Wireless were probably not surprised by this turn of events, because they already knew that the answer to that question was “yes”.
Who is Ashley Madison and Why Should I Care if She Was Hacked?
For those of you hearing about the Ashley Madison hack and wondering who the heck Ashley Madison is, well, first of all, it’s not a who, it’s a what, or, if you like, a where. Ashely Madison is ashleymadison.com, and it’s a ‘dating’ site for married people. Yes, it’s a hookup site for married people who want to play around or have an affair.
Yes Hackers Really Do Hack Baby Monitors
It sounds like urban legend: “Hacker hacks video baby monitor web cam and screams at little girl.” But it’s true, and it happens more often than you think, primarily owing to people putting their baby monitors web cams online and never changing the default password.
Can Your Car be Hacked through its Onboard Wireless?
With the increase in wifi in automobiles, coupled with onboard computing and tracki.. er, diagnostic capabilities, there has been a lot in the news lately about hackers wirelessly hacking cars. But how likely is it that your vehicle could be hacked?
Sony Movie “The Interview” Hack and Terror Threat Explained
Here is what is going on around the Sony hack tied to Sony’s ‘The Interview’ movie, and the The Interview threat from the Sony hackers. The Interview, with a Christmas release date, sees Seth Rogen and James Franco’s characters going to North Korea to interview North Korean leader Kim Jong Un, and convinced by the CIA to take the opportunity to kill Kim Jong Un. Ahead of its release, hackers hacked into Sony, grabbed all sorts of private employee and corporate data, including copies of the movie and other unreleased movies including Annie, Mr. Turner, Fury, and Still Alice, and then issued the following threat, including allusions to 9/11.
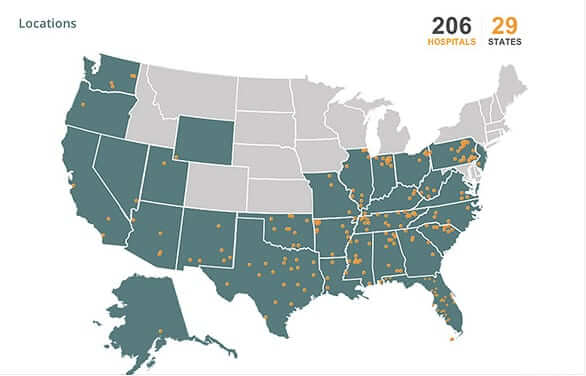
4.5 Million Hospital Records Hacked Across the U.S. – Complete List Here
4.5 million patient records at hospitals across the United States have been hacked, and their personal data stolen. Community Health System (also known as CHS and CHS.net) is a network of 206 hospitals across the U.S., operating under different names, in Alabama, Alaska, Arizona, Arkansas, California, Florida, Georgia, Illinois, Indiana, Kentucky, Louisiana, Mississippi, Missouri, New Jersey, New Mexico, Nevada, North Carolina, Ohio, Oklahoma, Oregon, Pennsylvania, South Carolina, Tennessee, Texas, Utah, Virginia, Washington, West Virginia, and Wyoming.
Apple Fingerprint Recognition Scanner Technology on the iPhone Already Cracked – But Does it Really Matter?
Mere days after Apple released the iPhone 5s, with its new “Touch ID” fingerprint identity sensor scanner, the Chaos Computer Club announced that it had “successfully bypassed the biometric security of Apple’s TouchID using easy everyday means”. But does this mean the fingerprint recognition technology is useless? We say not.