Category: Security
Saks Fifth Avenue, Lord and Taylor, Reveal 9 Month Long Credit Card Data Breach
In a hack that the New York Times is calling “one of the largest known breaches of a retailer”, Saks 5th Avenue and Lord and Taylor have had the credit card and debit card information of millions of customers compromised by an ongoing hack that lasted for months before it was terminated a few weeks ago.
“Why Can’t I Log Into My Account When I Know I am Using the Right Password?” This May be Why
Can’t log into your account via an app, or via the web, when you know that you are using the right password? In fact, when you try to log in using the exact same password on the web, or via the app, respectively (whichever one is not the one you are having trouble with) the password works perfectly? We may have the answer.
Do I Have to Worry About the Spectre Intel Chip Security Flaw? And What is Speculative Execution?
As news of the Intel chip security flaw has started to permeate public awareness, people are asking themselves two main questions: “Do I have to worry about it, and if so what do I need to do?” and “Just what is speculative execution?” (The issue with the chips has to do with the speculative execution function.) This flaw is said to affect millions of Windows, Mac, and Linux computers around the world. “Major flaw in millions of Intel chips revealed” screams the BBC headline. “A Critical Intel Flaw Breaks Basic Security for Most Computers,” banners Wired. Even Popular Mechanics is getting in on it, stating that “Horrific Security Flaw Affects Decade of Intel Processors.” Although, others are starting to say that it’s not limited to Intel chips, as pointed out by the Axios story, “Massive chip flaw not limited to Intel.”
How GDPR Will Conflict with Almost Everything
I was recently interviewed, in my capacity as an Internet law and policy attorney, and head of the Institute for Social Internet Public Policy, for an article sponsored by RSA about the impact that GDPR (the EU’s General Data Protection Rules), which goes into effect in the European Union in May 2018, is going to impact, well, everything. And, in particular, about how it will impact U.S. based businesses, because, trust me, it will.
Walmart Also Announces In-Home Delivery While You’re Not Home – And Puts Your Groceries Away for You
Amazon isn’t the only company looking to come into your home, literally, when you aren’t there. Walmart also has announced what they have nicknamed “in-fridge delivery”, a service where their employee, nicknamed a “Deliv driver” (seriously, Walmart, who is coming up with these things?) comes into your home to make deliveries, when you’re not home, even putting your groceries away in the fridge for you. To which we say not only “no”, but “hell no!”
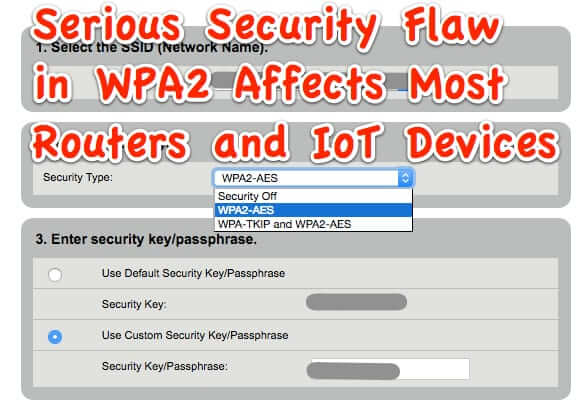
Major Vulnerability in Security Protocol for Most Wifi Routers and IoT Devices Revealed, Codename: KRACK
A newly announced exploitable security weakness in the WPA2 protocol is spelling trouble for most Internet wi-fi routers, including home routers, and Internet of Things (IoT) devices. The KRACK (Key Reinstallation Attacks) vulnerability in WPA2 has the potential for such widespread security incidents (because WPA2 is deployed nearly everywhere, and because this is not OS-specific, but attacks the router) that the revealing of it was coordinated among the researchers who have discovered it.
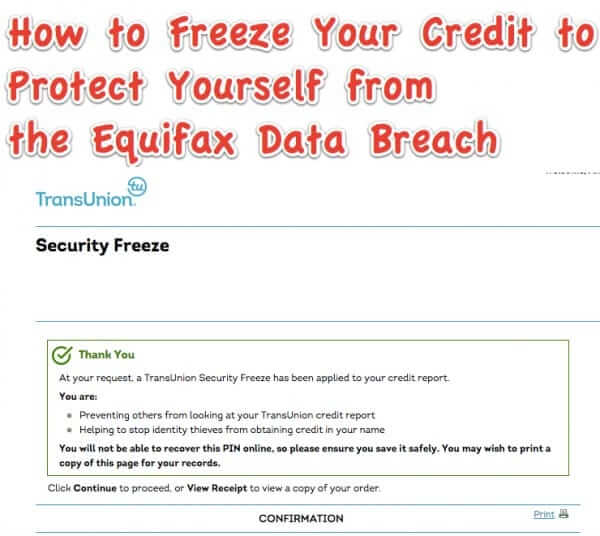
What YOU Need to do RIGHT NOW Because of the Equifax Data Breach in Order to Protect Yourself
Last week we started hearing about the Equifax data breach, although Equifax had actually known about the data breach at least a month earlier. (The full text of the Equifax statement about the cybersecurity data breach is reprinted below.) The most stunning thing about this breach is the breadth of it: the Personally Identifiable Information (PII), including names, social security numbers, and driver’s license numbers of 143 million U.S. citizens were exposed in this breach. Here is what you need to do, right now, to protect yourself.
Move Over White Collar and Blue Collar – the New Jobs in Town are ‘New Collar’
‘New collar jobs’ is the new trending buzzterm in employment, because it’s the new darling of the jobs world. ‘New collar jobs’ is essentially a euphemism for jobs which don’t require a college (let alone an advanced) degree. But not just any jobs – specifically tech jobs, and even more specifically, in some circles, cybersecurity jobs. In fact, in new Federal legislation that was introduced just a few weeks ago, it clearly states that the purpose of the bill is to take blue collar workers and re-educate them to become our nation’s industrial cybersecurity force.
Your Roomba May be Mapping Your Home and Sharing Your Home Map
iRobot, the company behind the Roomba vacuum, along with other cleaning robots, has sold 15 million of those little suckers worldwide. Part of the Roomba’s brilliance is mapping your house in order to be as effective and efficient as possible. However, many people are not aware of this mapping feature, and even those who are may not realize that the mapping data – i.e. the map of their home – is being sent back to iRobot HQ, and stored in the cloud. Nor have they likely realized that iRobot might like to share the map of their home with others. But that is exactly part of iRobot’s business strategy.
New Privacy Nightmare Camera-Enabled Amazon ‘Echo Look’ Lets Alexa Critique Your Wardrobe
We thought it was weird that Alexa will soon be able to detect your moods, and when we wrote about the hidden dangers of the Amazon Echo, we never dreamed that Amazon would up the ante by adding a hands-free video camera to the Echo! But that’s exactly what they’ve done with the Amazon Echo Look. And they expect you to use it in your bedroom, or bathroom, or wherever you get dressed, so that your Echo can give you wardrobe feedback with Amazon’s new Alexa-based ‘Style Check’ service.
Twitter Competitor Mastodon – the New Open Source Social Network – Explained
You may have recently heard about a new social network called Mastodon. Mastodon is an open source, completely free social network that is similar to, and on some level competing with, Twitter. However there are some important differences between Twitter and Mastodon. Here’s what Mastodon is, and what it isn’t.
What are Forged Cookie Attacks, and Why are They in the News?
There has been quite a bit in the news this week about “forged cookies” and “forged cookie attacks”, but little to actually explain them. A forged cookie attack is exactly what it sounds like though: a way for hackers to forge the information in your browser cookie, and when that information includes an authentication mechanism, voila! They can log into your account.
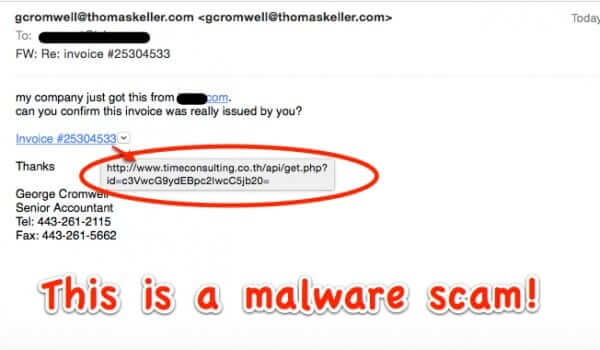
Do NOT Open Email Links from gcromwell@thomaskeller.com
A new malware scam is hitting email inboxes. The email sample that we have comes from an email address at thomaskeller.com (ours is specifically from gcromwell@thomaskeller.com), and claims to have received an invoice from your company. They even include your company name in the email, making it seem more legit. But it isn’t.
How to Install the Apple Security Update on Jailbroken Phones
You know you need to apply the urgent Apple security update on your jailbroken iPhone. While you can’t do it without restoring your iPhone to its unjailbroken state, it’s very easy to get the update installed and then rejailbreak your iPhone. Here’s our step-by-step tutorial for how to install the iOS security update on your jailbroken phone, with screenshots.
How to Check Whether Your Email Address is in the Exposed Ashley Madison Data
Now that the Impact Team hackers put the data of all 37 million Ashley Madison users online, you may be wondering how to check to see whether your email address is exposed in that data dump.