Category: Security
The 3 Things You Need to Know About the Heartbleed Bug
There has been a lot of urgent information circulating about the Heartbleed security bug (which some are mistakenly calling the “Heartbeat bug”) this week. But then you hear that the Heartbleed bug has been around for two years, and suddenly find yourself wondering why all the hype? Here are the three things that you need to know about the Heartbleed bug, and what you need to do about it.
RFID Chips in Your Credit Card: Electronic Pickpocketing – True of False?
There has been a lot of hysteria and misinformation surrounding RFID-enabled credit cards (also known as contactless or smart payment cards – or as some misidentify them – wifi credit cards). Also known as an “e-dip”, e-pickpocketing is possible, but highly unlikely – your old school credit card is far more likely to be duplicated than your RFID card is to be hijacked. Here are the facts as we know them.
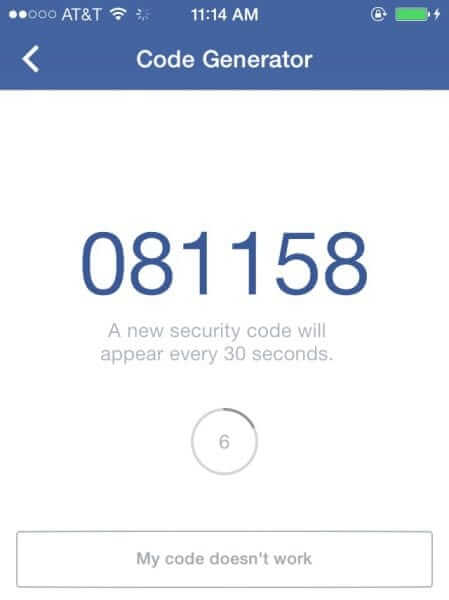
How to Find Facebook’s Text Message Authorization for 2-Factor Authentication
So you’ve set up 2-factor authentication at all of the places we’ve recommended, and now you can’t figure out how to get Facebook to send you the authorization security code text message to your mobile phone so that you can log into your Facebook account. Here’s where you need to find it.
Feinstein Says CIA Snuck on Computers, Deleted Documents – Why is Anyone Surprised?
This week there was an explosion in Washington, DC – specifically, Dianne Feinstein, chair of the Senate Intelligence Committee, exploded over documents vanishing from CIA provided computers at a CIA leased facility, and specifically relating to the CIA internal “Panetta Review”. While CIA director John Brennan and Feinstein argue, we can’t help but wonder: Just how naive do you have to be to believe that when the CIA produces documents on CIA provided computers, in a CIA leased facility, guarded by the CIA, that they won’t have left themselves a way to access those same computers? Or that they won’t use it?
Security Expert Dan Geer: We Are All Intelligence Officers Now (Full Text Here)
Last month, at the RSA Conference, computer security expert Dan Geer told the assembled security and cryptography experts “We are all intelligence officers now.” (RSA stands for Rivest, Shamir, and Adelman – Ron Rivest, Adi Shamir and Leonard Adleman together developed the RSA crypto algorithm.)
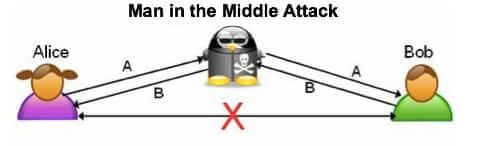
Millions of Iphones and iPads at Risk as Apple Rushes Security Update
Apple has released a critical security update for iPhone and iPad iOS 7 and iOS 6. This urgent update is to fix the critical security vulnerability that exposes your data (including usernames, passwords, and other account credentials at nearly any website or service) to a “Man in the Middle” (MitM) attack.
Talking Angela Facebook Message is a Hoax But There are Real Concerns
If you’ve seen the warnings on Facebook, you may be wondering “Is the Talking Angela app safe?” The Talking Angela app is basically safe for children, despite the revival of the Internet hoax chain letter on Facebook that is making the rounds. The post which is being shared around Facebook begins with “I cant even in words say what I just found out.. I am SHOCKED…” and goes on to tell how Talking Angela was caught asking their child inappropriate questions.
Kickstarter Hacked – Kickstarter Security Breach Leaked No Credit Card Information
The popular crowd funding source Kickstarter has just revealed – three full days after the fact – that owing to a security breach, Kickstarter was hacked. In an email letter to Kickstarter users, Kickstarter CEO Yancey Strickler announced the security breach, and assured users that “No credit card data of any kind was accessed by hackers.”
Why to Set Up Two-Factor Authentication (“2FA”) Everywhere You Can – Here’s Where
Here is why you must set up two-factor authentication (also called 2-step verification, or simply “2FA”) wherever you can. Many places now offer it, including Facebook, Paypal, Twitter, and, of course, Gmail (Google). You may in fact remember the story of how Naoki Hiroshima lost their Twitter account, valued at $50,000, to a hacker. Basically the hacker managed to get into and redirect Hiroshima’s email domain, allowing the hacker to do password resets on some of Hiroshima’s accounts, and intercept the password reset emails. It’s very easy for someone to do a password reset on an account if they have the email address, however with 2-factor authentication is becomes a lot harder.
Full Text of Obama’s Speech on NSA Phone Metadata Collection Program, January 17, 2014
In his speech regarding changes to the NSA’s Section 215 phone metadata collection and surveillance program, President Barack Obama stated outright, “I am ordering a transition that will end the section 215 bulk metadata program as it currently exists.” During his speech (full transcript below), President Obama also announced that the federal government will need to go to the the Foreign Intelligence Surveillance Court (FISA) every time that they want to search data, rather than relying on previous orders.
Target CEO Admits that Target Knew of Breach 4 Days Before Disclosing It
Target CEO Gregg Steinhafel said this week that Target knew about the massive security breach that put millions of Target customers at risk a full four days before Target notified their customers and the public about the breach.
4.6 Million SnapChat Passwords, Phone Numbers Stolen and Made Public – Nightmare for Parents
More than 4 Million SnapChat phone numbers, locations, and passwords have been stolen and leaked and made public. The database was put up on a site, SnapChatDB.info, where anybody could download the file. And while the site has been taken down, people who grabbed that file are already putting it to use.
Target Credit Card Breach: Data Stolen for All Sales Between 11/27 and 12/15
A massive Target credit card theft has just been announced. If you made a purchase at Target using a credit card or debit card at any time between November 27 and December 15, it is likely that your credit card number and your name, the card’s expiration date AND the card verification code (CVV) have been stolen.
NSA Surveillance Needs Oversight, Says President’s Review Group Report and Recommendations
The President’s Review Group, convened to address NSA surveillance and related issues revealed by Edward Snowden, has issued its report and recommendations on how to rein in and address the widespread, overbroad nature of NSA surveillance in general, and its trampling of privacy in particular, while at the same time addressing the genuine need for national security.
Millions of Facebook Passwords and Other Passwords Stolen in Massive Breach by Pony Botnet Controller
The Pony Botnet Controller virus – which may be on your computer – has stolen millions of Facebook passwords, Google passwords, Twitter passwords and Yahoo passwords, along with log-in credentials from email accounts and even FTP accounts. All told more than 2 million account usernames and passwords were stolen.