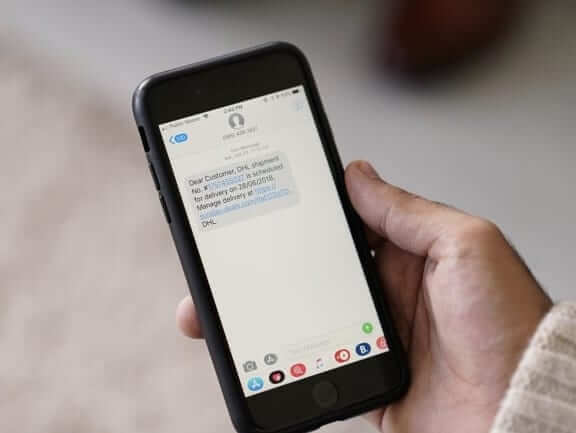
Because of spyware companies like the NSO Group, and their Pegasus spyware, it can now be fatal to click a link sent to you in a text message or email. That is what experts believe happened to Jamal Khashoggi, and perhaps almost to Omar Abdulaziz, who received a fake text message supposedly from DHL, and which experts believe installed the NSO Pegasus spyware on his phone.
We have repeatedly explained to our readers the dangers inherent in clicking links that you are not 100% certain came from someone you personally know, let alone in clicking on unexpected links. Just a few months ago we alerted people to the Netflix text message scam, and last year we warned of a text message scam that texted malicious links to people that, when clicked, stole their Facebook credentials from their phone.
But none of these previous text message scams had the potential to lead to someone’s death.
Citizen Lab, a Canada-based organization that focuses on, among other things, research, high-level strategic policy, and legal issues related to information, communications tech, and global security, has determined that Omar Abdulaziz, a Saudi dissident who is a permanent resident in Canada and who, tellingly, was in close communications with murdered Saudi journalist Jamal Khashoggi, “was targeted with a fake package delivery notification.”
According to CitizenLab, “We assess with high confidence that Abdulaziz’s phone was infected with NSO’s Pegasus spyware. We attribute this infection to a Pegasus operator linked to Saudi Arabia.”
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.
NSO is a spyware (“cyber security”) company based out of Israel. NSO sells its Pegasus spyware to governments for the purpose of, they say, fighting terrorism. CitizenLab has identified a Pegasus infection specifically coming from Saudi Arabia, and on Abdulaziz’ phone. Says CitizenLab, “we identified a suspected infection located in Quebec, Canada, operated by what we infer is a Saudi Arabia-linked Pegasus operator. We matched the infection’s pattern of life to the movements of Abdulaziz, and his phone, with his assistance. After examining his text messages, we identified a text message that masqueraded as a package tracking link. This message contained a link to a known Pegasus exploit domain.” {Emphasis our}
Fake DHL Link to Known NSO Pegasus Exploit Domain to Download Spyware on Target Phone
Eerily, Abdulaziz received a request from representatives of the Saudi government to ‘visit’ the Saudi embassy in Canada; one may imagine that Jamal Khashoggi was responding to a similar invitation the day he was murdered in the Saudi embassy in Turkey. But we digress…
There is little doubt at this point that Abdulaziz’ phone had not only been targeted but, via the fake DHL link on which he clicked, the NSO Pegasus spyware had been downloaded to his phone.
According to CBC Canada, “On two days, Citizen Lab found a perfect match between Abdulaziz’s movements between the gym and home, and the distinctive pings of the Pegasus infection it spotted in Quebec.”
Abdulaziz and Khashoggi were at this point exchanging messages almost daily, talking about ways to bring voices of dissent to Saudi Arabia, including a plan to send SIM cards that are hard to track to citizens in Saudi Arabia, so that they could safely access social media.
It isn’t just organizations in Canada who have determined that the bugging of Abdulaziz’ phone as a result of his clicking on that fake DHL link was directly connected to the killing of Khashoggi. Edward Snowden has also come out stating this, saying that NSO Group’s Pegasus spyware “was used to track and eventually murder Khashoggi at the Saudi Embassy in Istanbul,” and that “The reality is that they bugged one of his few friends and contacts using software created by an Israeli company,” allowing them to track Khashoggi even if he didn’t have the spyware installed on his own phone, and then lure him to their embassy in Istanbul.
Says CitizenLab, in an open letter to one of NSO’s majority investors, “The apparent sale by NSO Group of Pegasus spyware to Saudi Arabian government entities is alarming: while Saudi Arabia’s human rights record has long been abysmal, the Saudi government has taken increasingly aggressive action demonstrating a blatant rejection of human rights obligations in the face of international criticism. Such action includes the premeditated murder of Saudi dissident journalist Jamal Khashoggi inside the Saudi consulate in Istanbul, Turkey. Notably, Omar Abdulaziz and Jamal Khashoggi were in contact, working together on projects concerning human rights and democracy in Saudi Arabia”
Abdulaziz has now filed a lawsuit against NSO Group.
Now, the whole point of our writing this article is to point out that serious spyware can be installed on your phone – along with any number of other malicious things – simply by your clicking on a link in a text message.
In this day and age, it’s often nearly automatic to click on something you have received on your phone (where it’s even more difficult to discern the true sender than in email).
But it needs not to be.
Think before you click.
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.









