
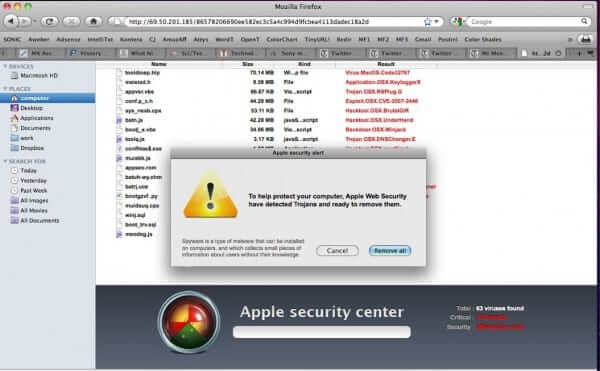
The “Security Alert” trojan, sometimes known as a ‘rogue antivirus’ attack, is making the rounds again. First spotted a few years ago, until recently the “web security” antivirus alert trojan targeted mainly PCs, tricking Windows users into downloading the evil ‘BestAntivirus2011.exe’ file by telling them that “To help protect your computer Windows web security have detected trojans and ready to remove them.” (Note the poor language usage.) Now this same tactic is being used to attack Mac users – all that has changed is the “Windows” to “Apple” and the file name (‘MacProtector.mpkg’ for Macs) – even the poor language remains the same! “To help protect your computer Apple web security have detected trojans and ready to remove them.” says the pop-up. Don’t fall for it, and whatever you do, don’t click on “Remove all”, which will cause the malware to be downloaded to your computer.
Fiendishly, the malware triggers a brand new browser window, which is made to look exactly like a Mac Finder window (on a Windows machine, it’s made to look like Windows Explorer), and then it puts the pop-up. You can see how people would be fooled, particularly when it looks like their own Finder or Explorer window, and it says that they have “detected trojans and ready to remove them.”:
Don’t fall for it; just close the page without clicking on any links or buttons, and you’ll be fine.
If you do happen to accidentally download it, the Mac trojan file you will want to remove is called “MacProtector.mpkg”, and the Windows one is called “BestAntivirus2011.exe”.
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.










How to proceed, once you have identified, that you are a victim of this malware:
If that Finder GUI faking webpage loaded in your web browser, it automatically caused your web browser to download some kind of file archive (ZIP, DMG, etc), which itself eventually contained MacProtector.mpkg (This is how it happened in my case)
1) Unpacking of this archive happened either:
a) Automatically according to your security-abuse generous browser settings. The name of that setting may vary from browser to browser, but must be labeled something like “open files after download” or “unpack file archives automatically”.
b) Or through your voluntary/accidental user interaction (double clicking it).
c) Or by exploiting a security hole in your web browser, which triggered something outside of the realm of the web browser on your local OS, which usually shouldn’t be possible, but the malware may found a way.
If your are at that stage, simply removing the file “MacProtector.mpkg” and the archive file it came in (in my case it was “anti-malware.zip”) is enough. Also erase that page from your browsing history to not accidentally return to it at a later time. And inform your friends about how they can recognize that malware, as we Mac users yet lived pretty unharmed by and therefore unaware of the malware issue, but as Macs got more popular in the recent years, I guess this carefree paradisiacal days are over.
2) If you or “it” somehow started the installation process for MacProtector.mpkg
a) Turn off your “sick” Mac immediately.
b) Temporarily get a second “healthy” Mac and a firewire cable. Connect them.
c) Start Sick Mac into target disk mode (hold “T” at boot time). Now Sick Mac’s hard disk is connected to Healthy Mac as an external hard disk.
d) Healthy Mac runs actively and has access to Sick Mac’s hard disk. Sick-Mac-HD now runs as a mere data disk but not as a system disk, I call this “passive mode”, but I am not sure whether that’s a technically correct term. Its data can be accessed (read / write), but none of its contained software (operating system, drivers and other background processes, and the potential malware) runs actively (in your RAM / CPU).
3) Run a malware scan (i.e. the freeware ClamXAV). Make sure its settings are something like “report infected files to me” or at most “move infected files to certain folder” but NOT “remove infected files right away” (as this may delete important data, into which you may be willing to put more recovery efforts, depends on the file and its value to you).
4) Back up important data, which you now reportedly know as uninfected.
5) Run the malware scan again, but this time more aggressively, with “heal files” and/or “erase files if they cannot be healed”.
The results of this step may vary. Possible outcomes:
a) Clean everything and regain your system complete and intact.
b) Reports as cleaned, but it may had to remove files relevant to system / driver / etc, and your system remains in a “crippled state”. A fresh installation is advised.
c) Reports that it could not remove the malware at all. This system should not be trusted anymore. A fresh installation is necessary!
6) Fresh installation and data restoration from your backup medium.
OK – So I clicked on it. So it dumped into my cpmuter, I am assuming. How do I get rid of it if my computer is infected now? I did remove macprotector.mpkg from my files. Is there anything else I need to do?
Thanks so much.
Sandy
AKA Dingbat…..
Thanks for this documentation!
My mother got a victim of this malware, but luckily she was suspicious early enough, called me, and I instructed hear to immediately power down the computer.
I then investigated the hard disk in passive (=reading) mode from an auxiliary computer, had a look through the most important log files and directories, and eventually ran a ClamXAV scan, which detected this malware, identified its name, and my search brought me here.
Thanks!