The Dyre Wolf phishing malware targets primarily businesses and organizations (rather than individuals). This is because it tricks the victim into giving up bank credentials, and then does a wire transfer. However it works by tricking individuals using social engineering, which is also how it gets around 2 factor authentication (2FA). Dyre Wolf is distinct from the dire wolf – Dyre Wolf is phishing malware, the dire wolf is an extinct member of the wolf family (and the direwolf is a mythical dire wolf featured in Game of Thrones).
As a reminder, we recommend that you set up 2 factor authentication wherever you can. But that isn’t going to protect you if you fall prey to social engineering, such as being tricked into giving up your mother’s maiden name (often used for security questions) or your childhood telephone number (ditto).
How Dyre Wolf Works
The Dyre Wolf malware is first installed on a machine within the target organization by another piece of malware called Upatre. Upatre gets installed on an individual employee’s or other individual’s machine in the company by being emailed to that individual. Once Upatre is on the machine, it installs Dyre Wolf.
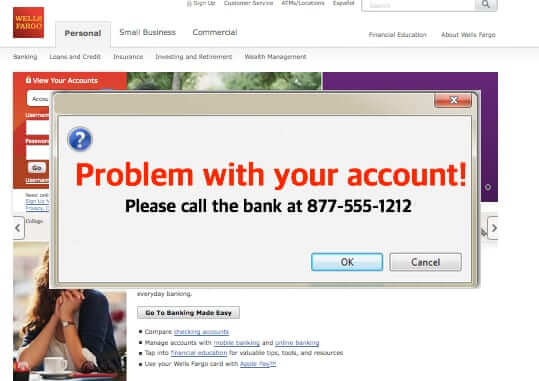
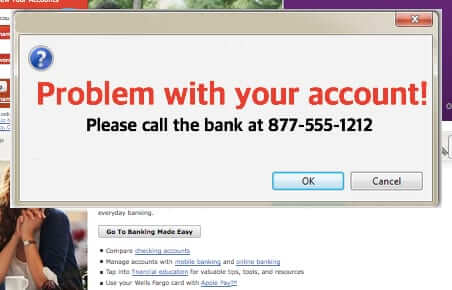
Dyre Wolf is diabolical in that it invokes fake log-in screens for many different banks, so that when the individual in the organization types the URL of the company’s bank, Dyre Wolf puts up a screen that looks like the victim’s bank. The fake login screen says that there is a problem with the target’s bank account, and to call the number displayed on the screen.
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.
Mockup of a Dyre Wolf bank screen
When the victim calls the number, someone on the other end of the line pretends to be with the victim’s bank, and using social engineering, gets enough information to actually log into the bank account. Once in the target’s bank account, a fraudulant wire transfer is initiated. Then a DDOS may be initiated against the victim’s website, presumably both to keep them from logging into the bank, and to distract them from discovering the transfer in a timely manner.
Organizations that have been the victim of Dyre Wolf have experienced fraudulant wire transfers of as much as $1.5million USD.
According to security researcher John Kuhn, who first wrote about Dyre Wolf at the end of last week, “As soon as the victim hangs up the phone, the wire transfer is complete. The money starts its journey and bounces from foreign bank to foreign bank to circumvent detection by the bank and law enforcement.”
One of the primary problems here is that individuals – in this case employees or other personnel within the organizations – are falling for the social engineering. As we elaborate in our article about the odds that your hacked data will be used, “one of the biggest data security threats is still internal to companies: their employees.”
In other words, human error.
While we all (hopefully) know not to fall for the links in email that seem to be from a financial institution, the Dyre Wolf phishing scam takes it to a whole new level by using (and staffing!) a telephone line, the number for which is displayed on what seems to be the bank website.
Businesses need to train their employees to be ever-vigilent, but perhaps they need to go further, perhaps making only one person responsible for having the banking credentials, and then providing extra security training for that person. Or, even, not having access to online banking at all.
The Internet Patrol is completely free, and reader-supported. Your tips via CashApp, Venmo, or Paypal are appreciated! Receipts will come from ISIPP.